We recently took a shot in this year’s RootCon 18 CTF Pre-Qualifiers and had a lot of fun solving the challenges. In this post, I’d like to share a brief writeup of the challenges our team was able to solve including the scripts that I have wrote to solve the challenges.
Big shoutout to my friends jmrcsnchz and damaidec for pushing through the CTF and solving these tricky challenges with me!
Super Secure Static Website
Visiting the ip and port given to us, we see a login page. I initially tried random credentials but nothing worked and just showed 405 method not allowed. So we tried changing the request to GET but still it did not work.
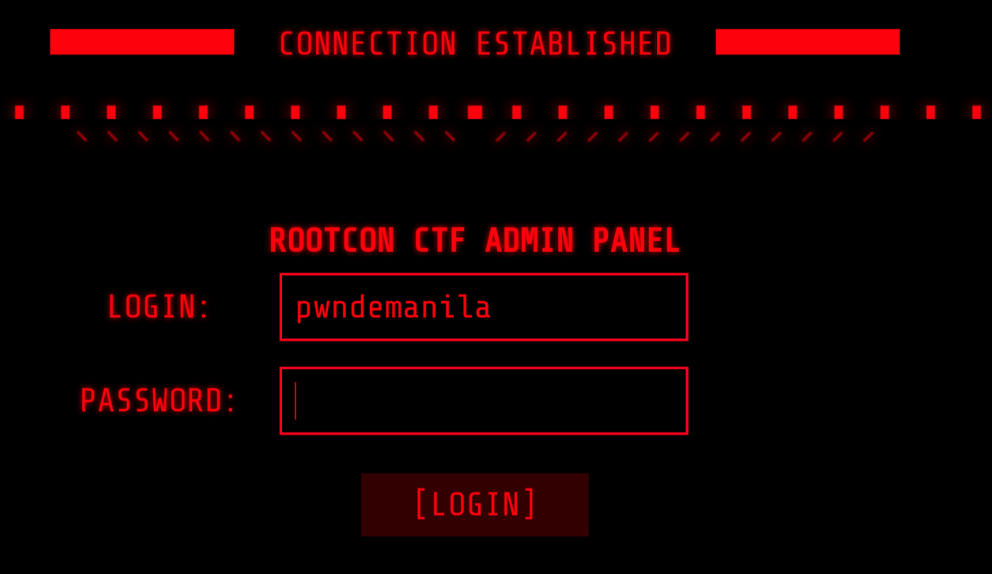
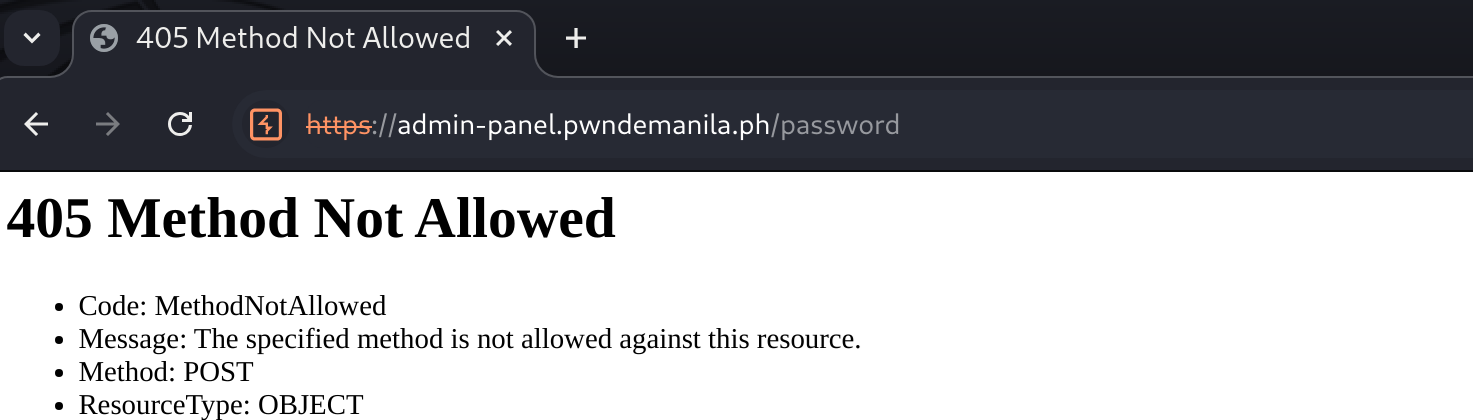
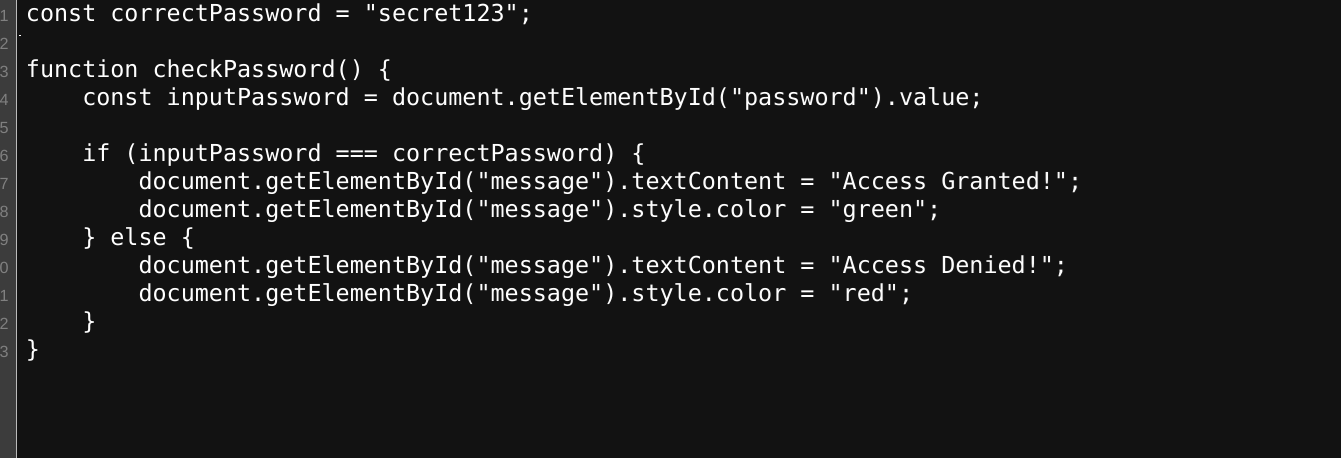
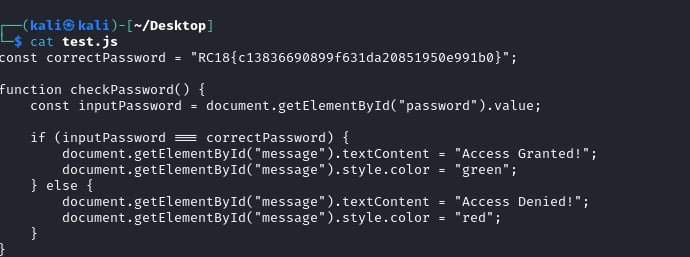
Looking also at source, we see that there is a js file that contains a hardcoded password but upon trying this password on the login page, it still did not work.
So investigating more, we discovered that this web application is hosted on AWS, so we focused on that. We queried the version of the objects and then queried the contents of each of the versions and found the flag in one of them.
aws s3api list-object-versions –bucket admin-panel.pwndemanila.ph
aws s3api get-object –bucket admin-panel.pwndemanila.ph –key script.js –version-id 3m838_45RnoGWi9ssn0xV90xdwzU1Zh8 test.js
Run
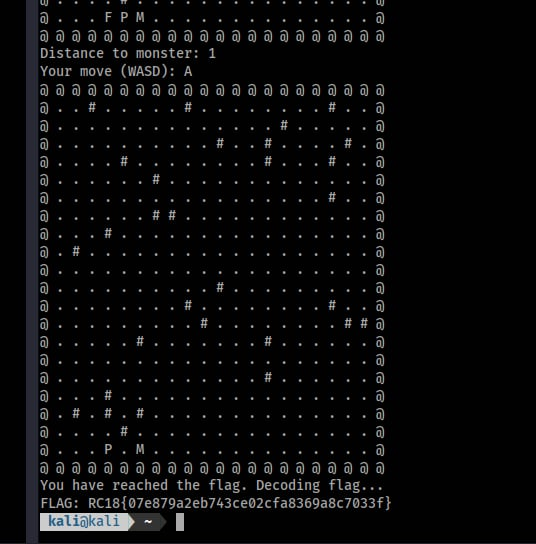
This challenge was a bit confusing for us since it did not give any clear indications for exploitation. It just showed a big maze with the instruction as shown below
Reach the flag (F) while avoiding the monster (M). Use WASD to move (W=up, A=left, S=down, D=right).
@ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ . . # . . . . . # . . . . . . . . # . . @ @ . . . . . . . . . . . . . . # . . . . . @ @ . . . . . . . . . . # . . # . . . . # . @ @ M . . . # . . . . . . . . # . . . # . . @ @ . . . . . . # . . . . . . . . . . . . . @ @ . . . . . . . . . . . . . . . . . # . . @ @ . . . . . . # # . . . . . . . . . . . . @ @ . . . # . . . . . . . . . . . . . . . . @ @ . # . . . . . . . . . . . . . . . . . . @ @ . . . . . . . . . . . . . . . . . . . . @ @ . . . . . . . . . . # . . . . . . . . . @ @ . . . . . . . . # . . . . . . . . # . . @ @ . . . . . . . . . # . . . . . . . . # # @ @ . . . . . # . . . . . . . # . . . P . . @ @ . . . . . . . . . . . . . . . . . . . . @ @ . . . . . . . . . . . . . # . . . . . . @ @ . . . # . . . . . . . . . . . . . . . . @ @ . # . # . # . . . . . . . . . . . . . . @ @ . . . . # . . . . . . . . . . . . . . . @ @ . . . F . . . . . . . . . . . . . . . . @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @ @
Distance to monster: 27 Your move (WASD): …
I am not exactly sure if this is intended or on how exactly this challenge should have been solved, but my teammate just reset the game multiple times to get a favorable starting position and just played the game normally. After your player reaches the flag, the flag was also then shown.
Zippy
After downloading the given file, I tried and extracting the contents of it and it showed another zip file. This indicated that I need to recursively unzip the contents of this file and MAYBE the last file contains the flag. So I developed a bash script to automate this for me as shown below
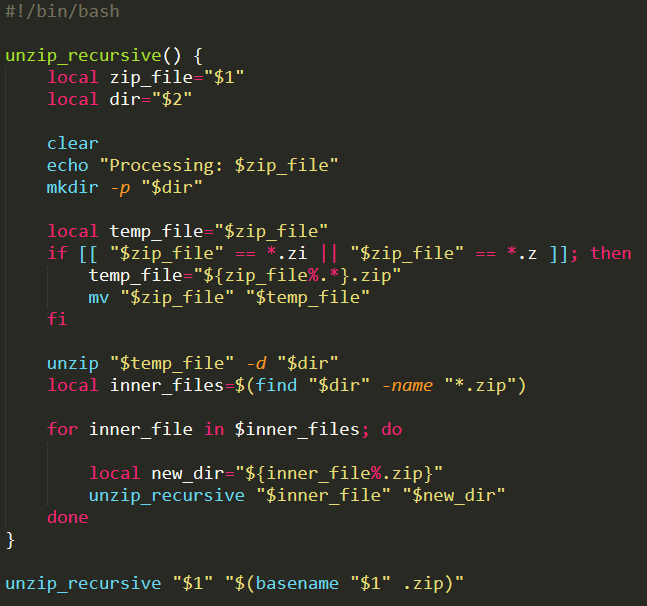
So after running it for a while, my script showed that the last file is empty. I initially thought that this challenge might have been broken since there is no flag whatsoever.
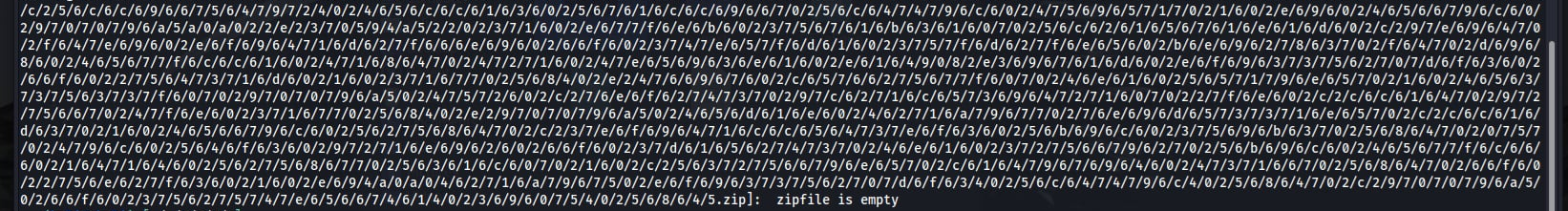
However, we realized that the names of the folders might be hex encoded since they only contain the characters 0-9 and a-f. So collecting these and passing it through cyberchef and hex decoding it did NOT get us anywhere :(
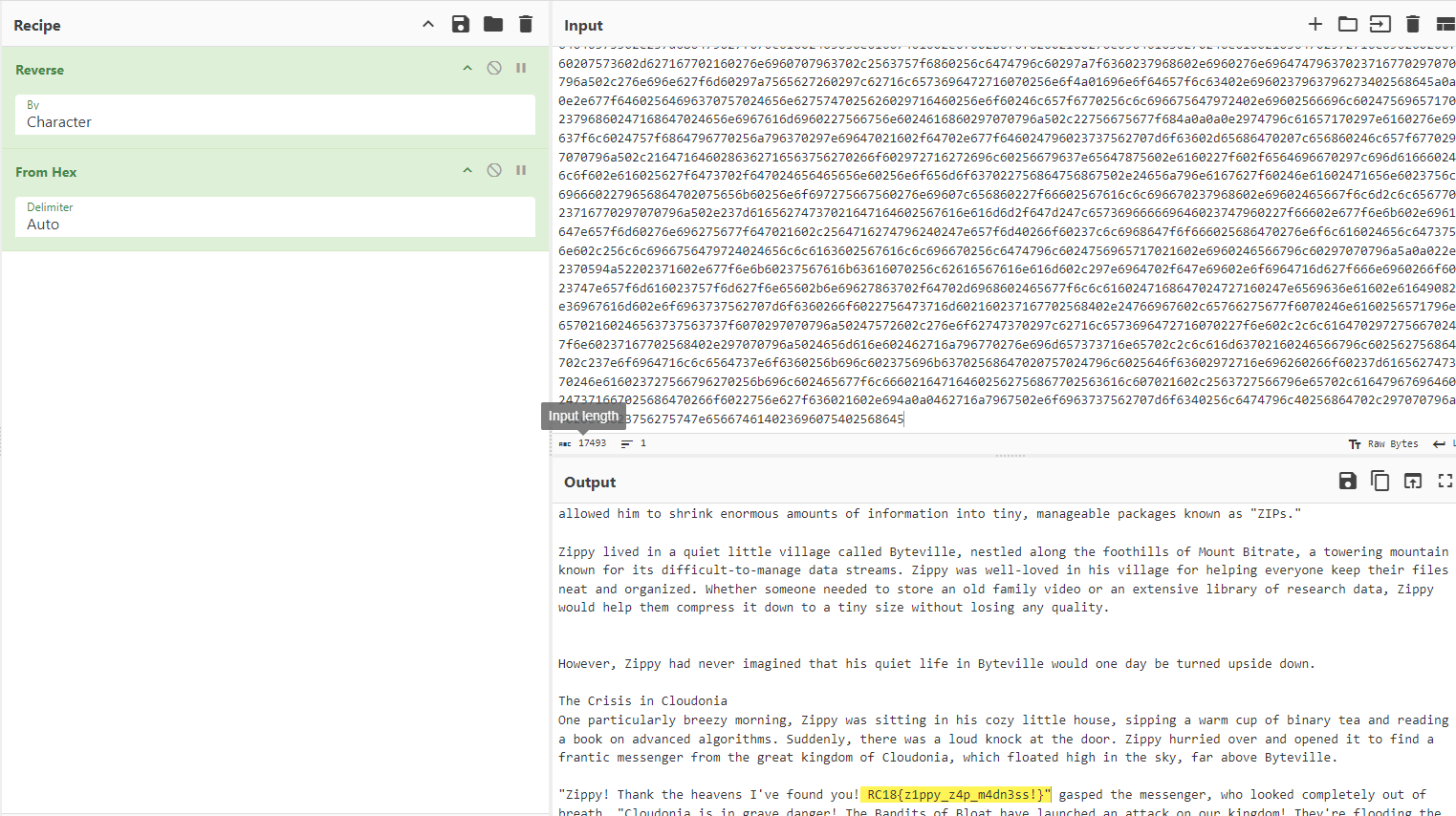
It was then further discovered that the output should be first reversed before being hex decoded and we get the flag from there
I Can See The End
This one was a bit tricky since the only thing that was provided to us was a png file so we immediately assumed that this was related to steganography.
Looking at this png and checking different variations of it did not provide any progress.

Later on, we have discovered that there is this tool called zsteg that detects stegano-hidden data specifically in PNG & BMP, which exactly fits our file! Running “zsteg -a -l 0 see.png” command gave us some output that kinda resembles the flag
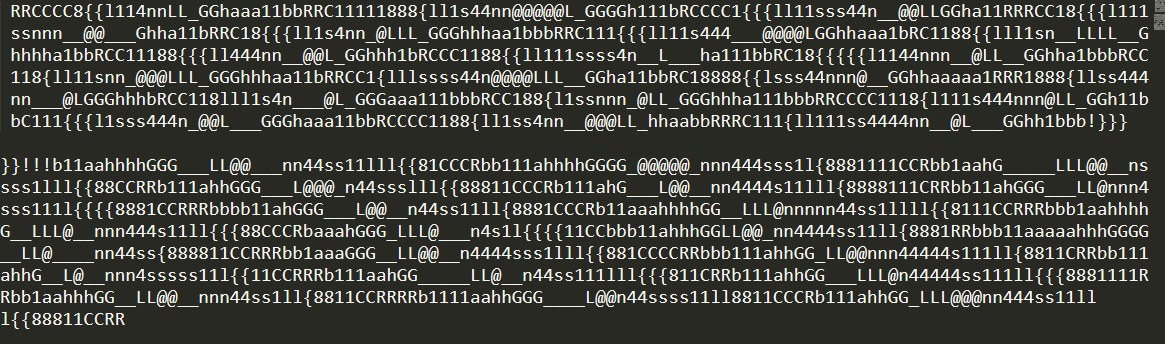
Trying to decipher/guess this, I have came up with
- lianl ghaib
- lisn all ghai
- lisanal ghaib
- lisan lghab
- and many more…
Searching about this thing, I found this https://dune.fandom.com/wiki/Lisan_al_Gaib
So at this point, it was just about finding the right combination of characters and we get the flag: RC18{l1s4n_@L_Ga1b!}
Rock Paper Scissors
This was another fun one because this involved winning a rock, paper, and scissors match for 1000 games consecutively and obviously we need to automate to do this again and again.
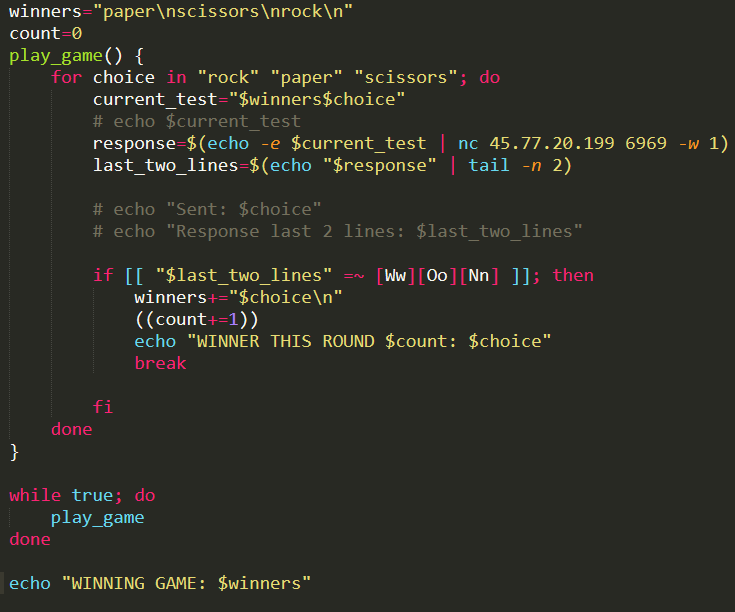
Observing how the mechanism of this works, it shows YOU WON if you obviously won against the opponent, and it showed YOU LOSE THIS ROUND when you tie or lose. We can leverage this by just bruteforcing rock, paper, and scissors and see if you win or lose and recording that. So I again made a script for this as shown below
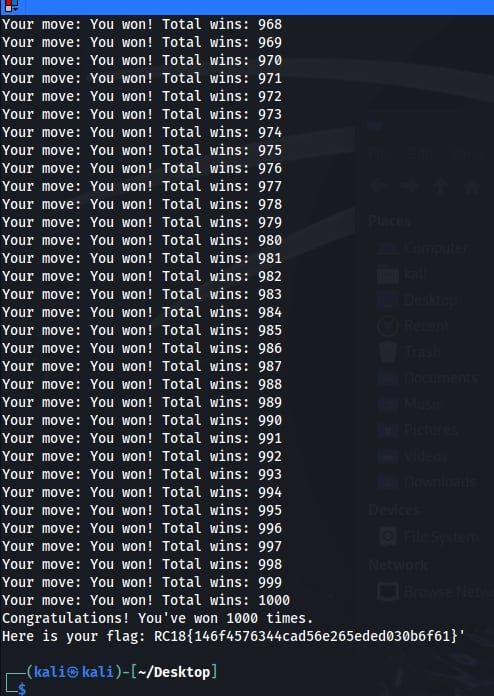
So running this for a while and getting all the winning moves, we get the flag
Beelzebub
This was a very fun challenge since it was a binary file! So let us try and run this and see what we get
Initially it is looking for a shared library called “libcrypto.so.1.1”, so we fetch that and install it on our machine
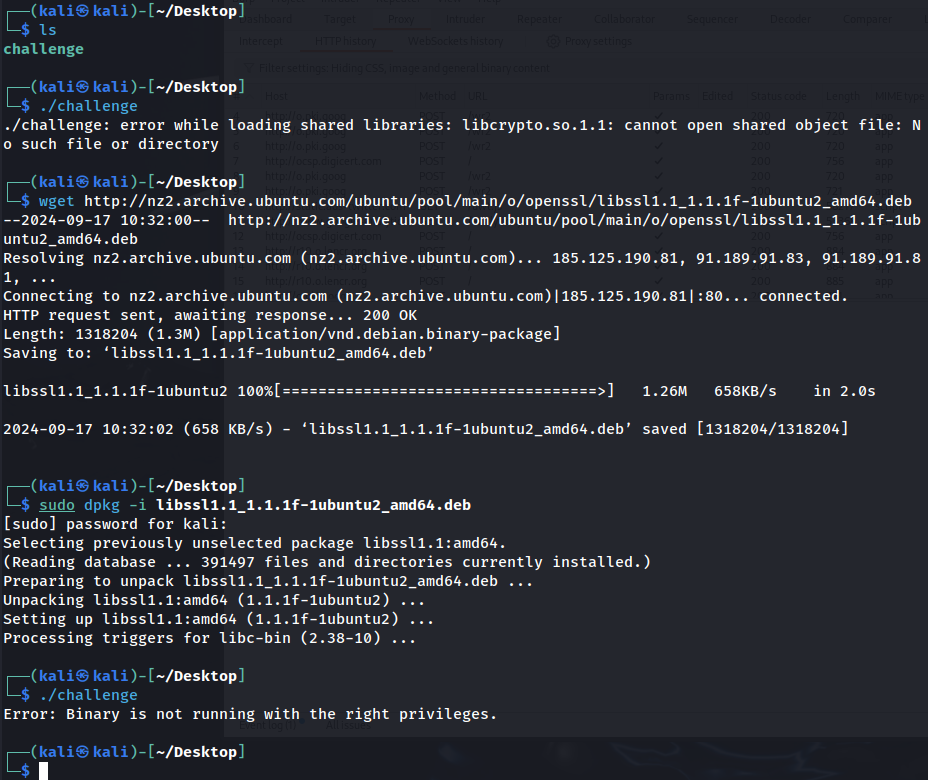
After that, it looks for the right permissions, but we do not know what permissions is it looking for, so we try and reverse engineer this binary using ghidra
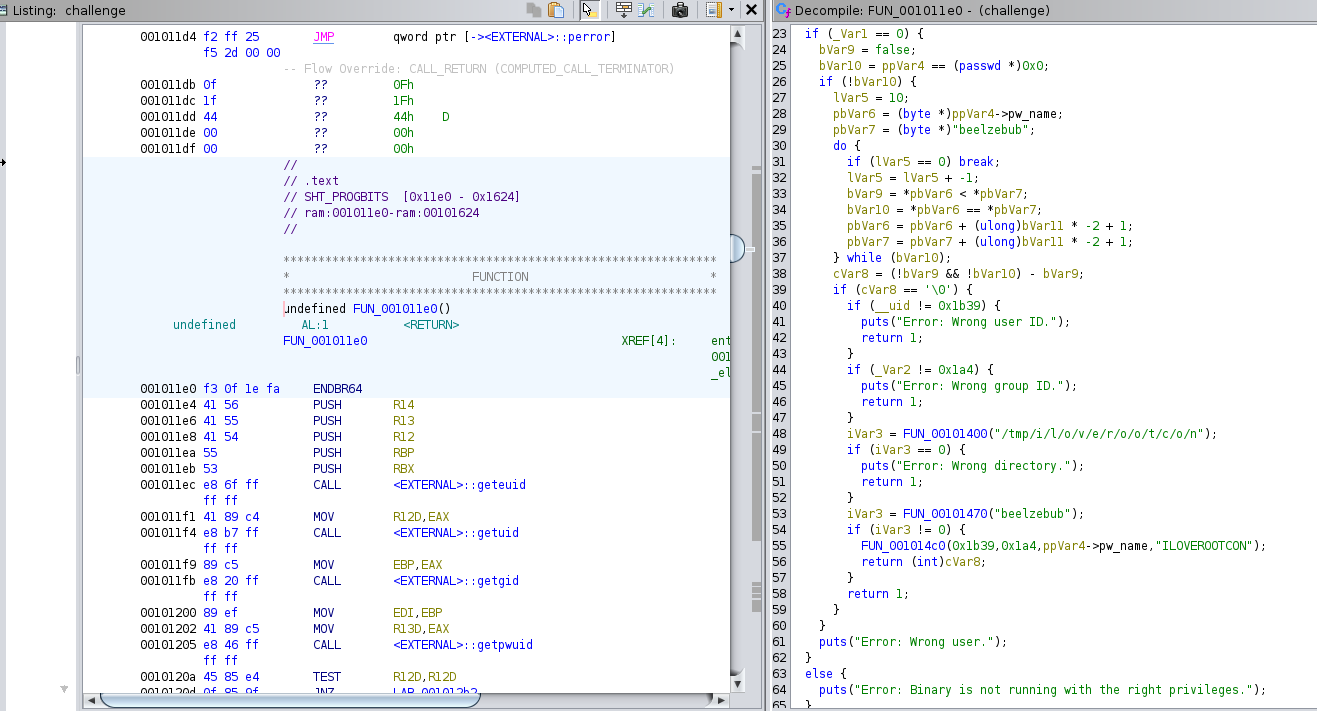
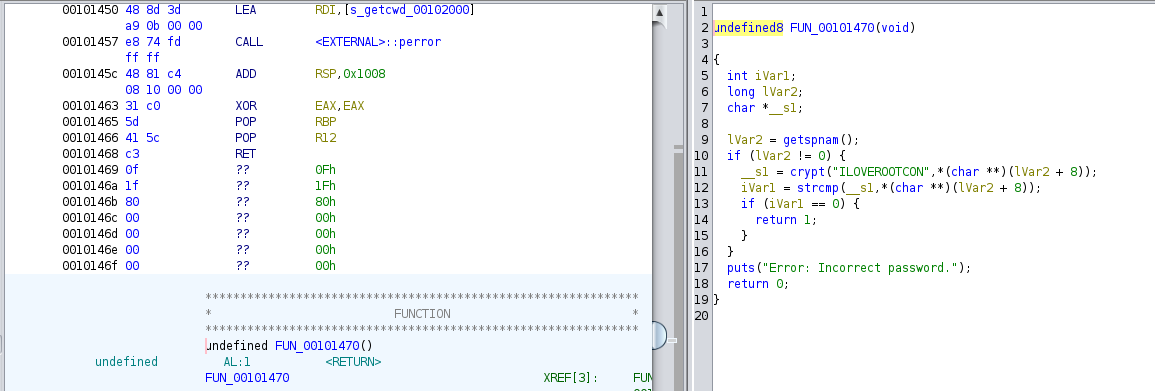
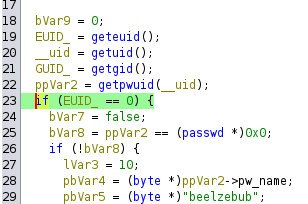
We see here that we need to first be running as the user beelzebub with password ILOVEROOTCON
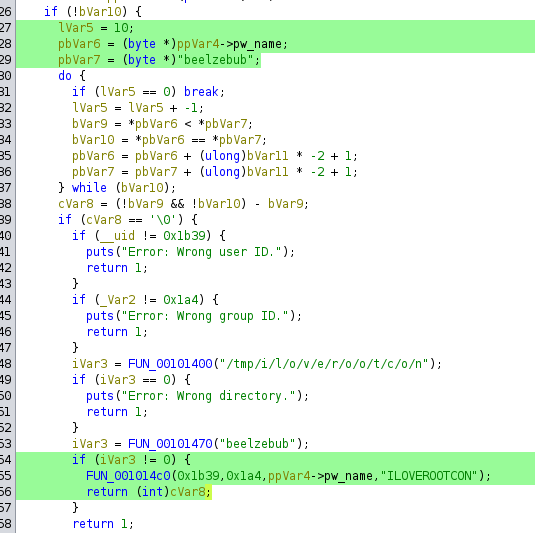
Next we see that we need to have the following
- uid 0x1b39 (6969 in decimal) or else it would say “wrong user ID”
- gid of 0x1a4 (420 in decimal) or else it would say “wrong group ID”
- euid of 0 (on the if statement)
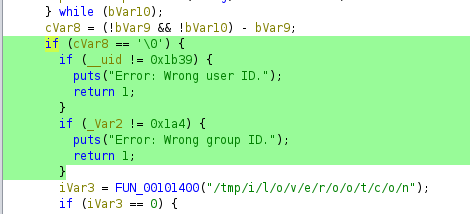
Next on the list is that the binary should be in the /tmp/i/l/o/v/e/r/o/o/t/c/o/n directory
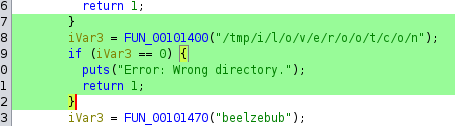
Now assuming that all the setup was done correctly, running this binary should show us the flag